How to configure WAF log integration (old method) for AWS WAF v2
AWS WAF v2Old PlanNew PlanLegacyUsage
Overview
There are two methods of WAF log retrieval: the new method and the old method.
The new method allows users to enable WAF log-related features by opting in with a WAF log retrieval checkbox.
The old method is the same as the one available on the old WafCharm Dashboard, which uses Lambda to transfer WAF logs.
If you are using the Legacy rule policy, you can use both, but it is recommended to switch to the new method.
WAF log retrieval is optional.
There are two ways to configure if you choose the old method.
- Exporting WAF logs directly to an S3 bucket
- Using Amazon Data Firehose to export WAF logs to an S3 bucket
Please keep in mind that WAF log retrieval does not support WAF logs outputted via CloudWatch Logs.
Preparations
To use the old method, you are required to create an IAM role and configure Lambda on the AWS management console. Therefore, the AWS account you use on the AWS management console must have the permissions listed below.
If you have permissions equivalent to the ones listed below, you should be able to complete all the steps.
- Exporting WAF logs directly to an S3 bucket
- AWSLambda_FullAccess
- IAMFullAccess
- CloudWatchFullAccess
- Using Amazon Data Firehose to export WAF logs to an S3 bucket
- AWSLambda_FullAccess
- IAMFullAccess
- CloudWatchFullAccess
- AmazonKinesisFullAccess
Notes
- It is recommended that you periodically (e.g., every month) transfer WAF logs outputted to your S3 bucket to S3 Glacier or delete them using the life cycle feature.
- If you want to confirm that the WAF logs are successfully transferred to WafCharm, please check the two points below, and send the latest WAF log file name and the target Web ACL ID to the WafCharm support team.
- WAF logs are outputted to your S3 buckets.
- There are no error logs in the CloudWatch event logs (START/END/REPORT lines should be logged when an event is triggered)
- How to check for an error
- Open CloudWatch -> Open Log groups -> Open
/aws/lambda/Lambda function name-> Click on the latest log stream (available at the top of the list) -> Check if any lines contain the word "ERROR"
- If you edit the IAM role/policy after you have deployed the Lambda, the changes made to roles or policies may not be applied to the working Lambda scripts. In that case, please add an empty line at the bottom of the index.mjs and click the [Deploy] button again.
- If you have registered WAF Configs (web ACLs) for different AWS WAF versions (Classic or v2) on WafCharm and wish to use this feature for both WAF Configs, please prepare separate Amazon Data Firehose and Lambda for each AWS WAF version.
- If the AWS WAF version is the same, you can share Amazon Data Firehose and Lambda between multiple web ACLs.
- The content of index.mjs for AWS WAF v2 and AWS WAF Classic are different.
- Log filtering provided by AWS WAF is not recommended if you wish to use this feature.
- If you filter WAF logs to only save logs with action: Block
- Only WAF logs with blocked requests are available, so the monthly report and detection notification operate based on the blocked logs.
- If you filter WAF logs to only save logs with action: Count
- The monthly report and the detection notification will not work properly because the Count action for a single rule and rule group are treated differently by AWS WAF in WAF logs.
- If you filter WAF logs to only save logs with action: Block
Procedure
Exporting WAF logs directly to an S3 bucket
How to use the feature
The architecture overview is as follows.

AWS WAF will output WAF logs directly to an S3 bucket on your AWS environment.
When WAF logs are output to an S3 bucket (S3 putObject Event Trigger), it triggers the Lambda to execute the script.
The data is transferred to WafCharm and monthly reports can be created and viewed without any additional configurations at the beginning of each month.
If you configure email notification settings for WafCharm rule detections on the WafCharm Console, you can use the WAF log alert (notification detection) feature.
Output WAF logs on AWS WAF
- Sign in to the AWS management console.
- Open the list of web ACLs on AWS WAF.
- Open the target web ACL.
- Click [Logging and metrics].
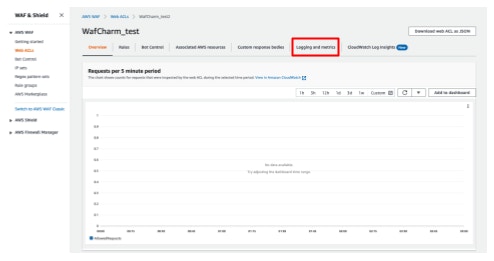
- Click [Enable].
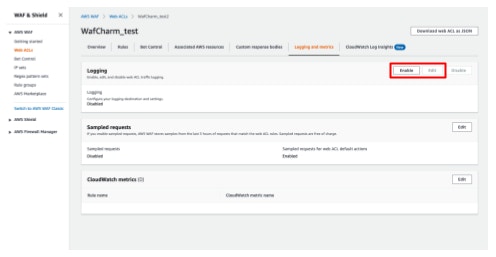
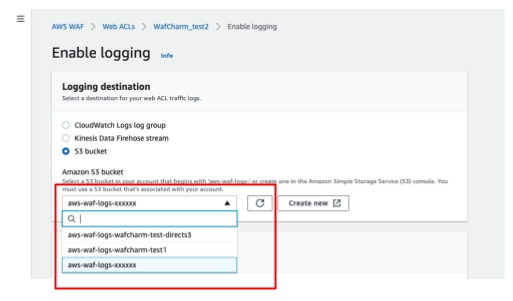
- Select [S3 bucket] under [Logging destination].
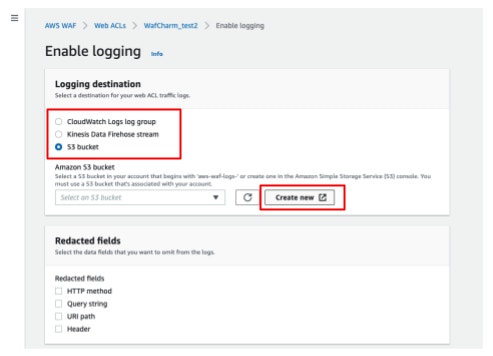
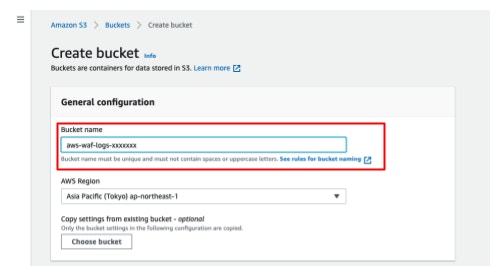
- Click [Create new] on the [Amazon S3 bucket] section.
- Enter a name that begins with [aws-waf-logs-] in [Bucket name].
Per AWS specification, you are required to add [aws-waf-logs-] at the beginning of the S3 bucket name.
- Go back to the AWS WAF page and select the S3 bucket you just created from the drop-down menu.
- Click [Save].
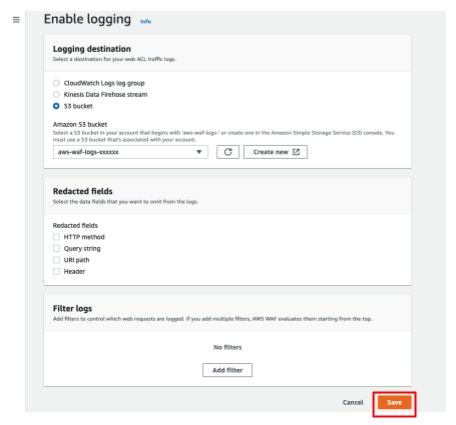
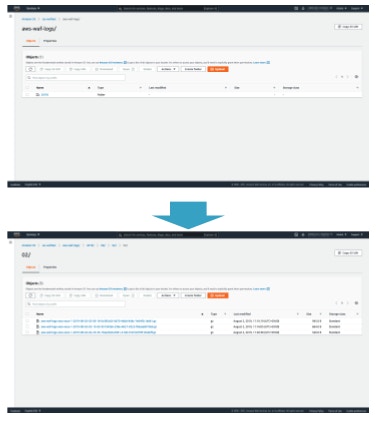
- Access the target resources and make sure that WAF logs are outputted to the expected S3 bucket.
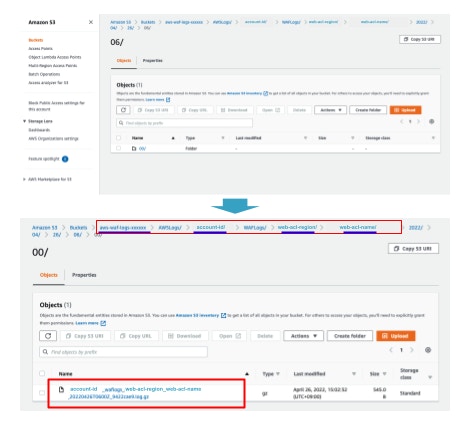
- Open the S3 bucket and check the path where WAF logs are outputted.
The format should be like below. You will use this information later.
aws-waf-logs-[specified bucket name]/AWSLogs/account-id/WAFLogs/Region/web-acl-name
Other than the S3 bucket name, account-id, Region, and web-acl-name should change based on your environment.
Create an IAM policy and role used by Lambda
You will be creating the three items below.
- Read permissions to your S3 bucket.
- Put permissions to transfer WAF logs to WafCharm's S3 bucket.
- The IAM role with the permissions above to be used by Lambda.
- Open IAM.
- Create a Read permission to your S3 bucket.
- Open [Policies] and click [Create policy].
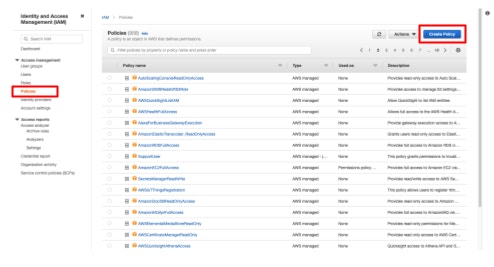
- Configure the options below.
- Service: S3
- Action: GetObject
- Resources:
arn:aws:s3:::aws-waf-logs-bucketname/AWSLogs/account-id/WAFLogs/Region/web-acl-name/*Write the S3 bucket path you obtained in the previous steps. The path specified under the [Resources] must end with
/*.
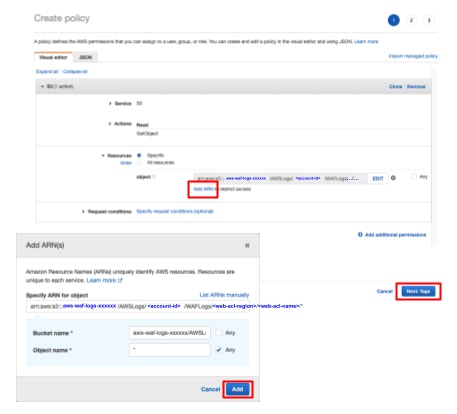
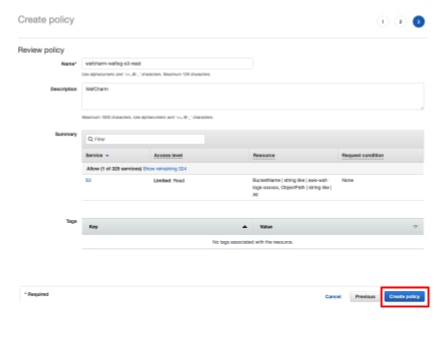
- Proceed to the Review policy page and enter the policy name and description (optional).
The name can be any value.
Example: wafcharm-waflog-s3-read
- Open [Policies] and click [Create policy].
- Create a Put permissions to transfer WAF logs to WafCharm's S3 bucket.
- Open [Policies] and click [Create policy].
- Configure the options below.
- Service: S3
- Action: PutObject, PutObjectACL
- Resources:
arn:aws:s3:::wafcharm.com/*Specify WafCharm's S3 bucket to transfer WAF logs.
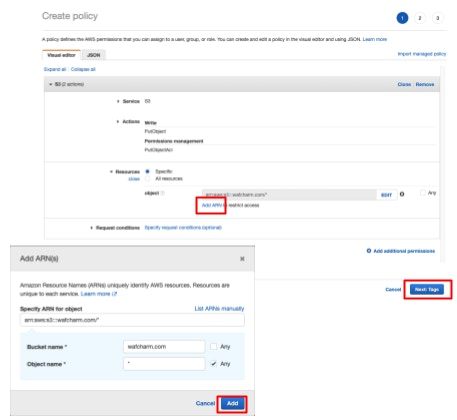
- Proceed to the Review policy page and enter the policy name and description (optional).
The name can be any value.
Example: wafcharm-waflog-s3-put
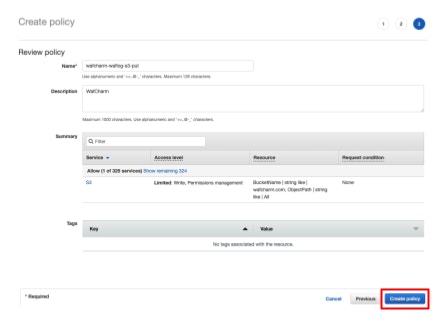
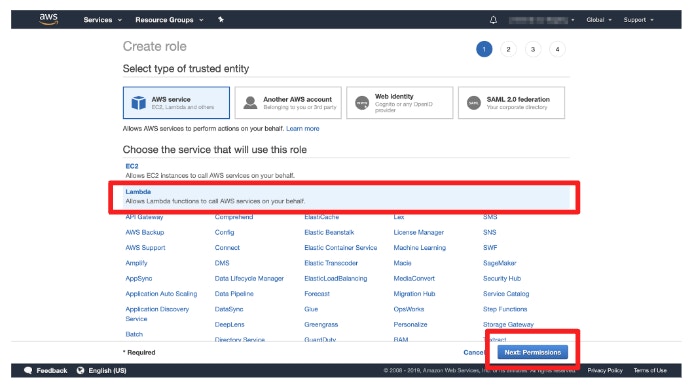
- Create an IAM role for Lambda.
- Open [Roles] and click [Create role].
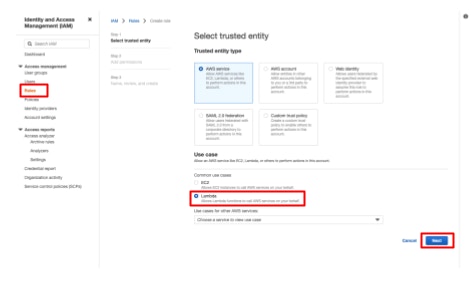
- Choose [Lambda] for [Use case].
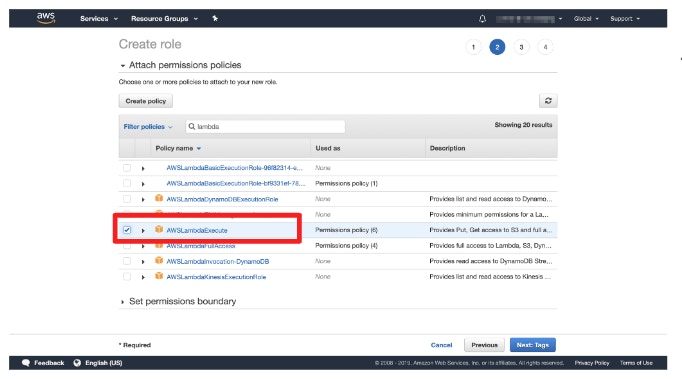
- Search for the permissions below under [Permissions policies] and check to add them.
- AWSLambdaExecute
- Read permission created in the previous steps (e.g.: wafcharm-waflog-s3-read)
- Put permission created in the previous steps (e.g.: wafcharm-waflog-s3-put)
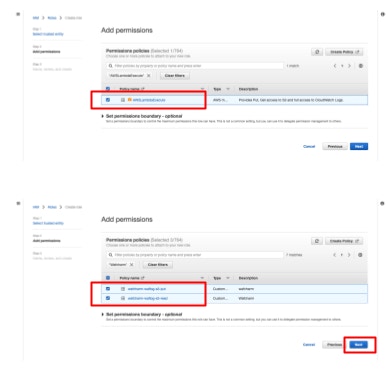
- Proceed to the next page and enter the role name and description (optional).
The name can be any value.
Example: wafcharm-waflog
- Open [Roles] and click [Create role].
Configure Lambda
- Switch to the same region as your S3 bucket.
- Open Lambda.
- Click [Create function].
- Enter [Function name].
The name can be any value.
Example: wafcharm-waflog
- Configure the options below.
Runtime: Node.js 20.x ~ Node.js 24.x
Execution Role: Use an existing role
Existing role: Select the IAM role you created in the previous steps (e.g.: wafcharm-waflog)
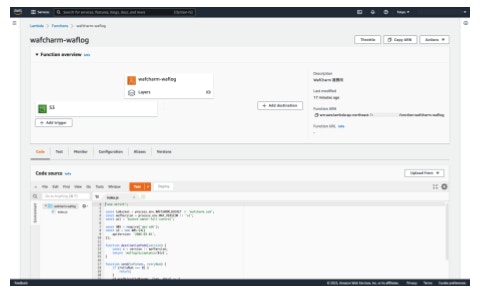
- Click [Create function].
- Paste the index.mjs available below in the editor under the [Code source].
- Click the [Deploy] button.
- Click the [Add trigger] button.
- Configure the options below.
Select a source: S3
Bucket: the S3 bucket you created in the previous steps
Event types: All object create events
Prefix:
AWSLogs/account-id/WAFLogs/Region/web-acl-name/The account-id, Region, and web-acl-name should change based on your environment.
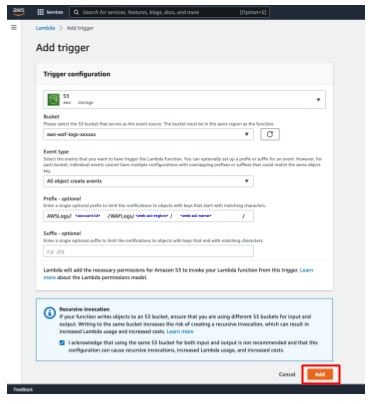
- Click [Add].
- Click [Configuration].
- Click the [Edit] button to the right of [General configuration].
- Configure the options below.
Description (optional)
Timeout: 1 minute
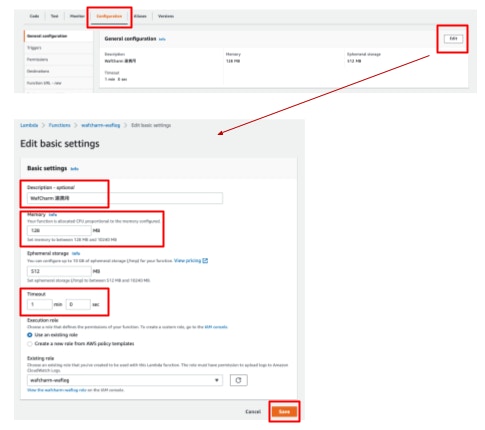
- Click [Save].
Configure the retention period for Lambda's execution logs on CloudWatch Logs
This configuration is optional.
If you want to change the retention period for your logs, please follow the steps below.
- Execute the Lambda script.
Access the target resources to output WAF logs. The Lambda script is triggered when the WAF logs are outputted to the S3 buckets.
- Open CloudWatch.
- Click [Log groups].
- Check the checkbox of the Lambda's log group.
- Click [Edit retention setting(s)] from the [Action] menu.
- Change the period under the [Expire events after:] drop-down menu.
The default is set to [Never expire]. Please adjust the period as necessary.
Using Amazon Data Firehose to export WAF logs to an S3 bucket
How to use the feature
The architecture overview is as follows.

AWS WAF will output WAF logs to an S3 bucket via Amazon Data Firehose on your AWS environment.
When WAF logs are output to an S3 bucket (S3 putObject Event Trigger), it triggers the Lambda to execute the script.
The data is transferred to WafCharm and monthly reports can be created and viewed without any additional configurations at the beginning of each month.
If you configure email notification settings for WafCharm rule detections on the WafCharm Console, you can use the WAF log alert (notification detection) feature.
Configure Amazon Data Firehose
- Sign in to the AWS management console.
- Switch to the same region as your web ACL.
If you are attaching CloudFront to your web ACL, select US East (N. Virginia).
- Open [Amazon Data Firehose].
- Click [Create Firehose stream].
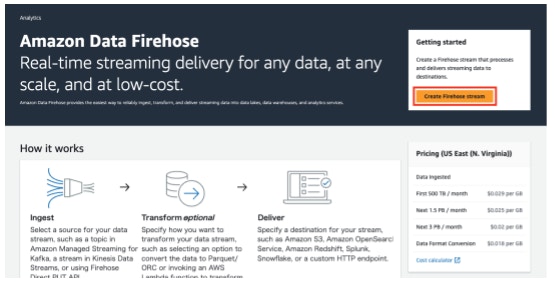
- Select the options below under the [Choose source and destination] section.
- Source: Direct PUT
- Destination: Amazon S3
- Firehose stream name: enter a name that begins with [aws-waf-logs-]
Per AWS specification, you are required to add [aws-waf-logs-] in the beginning of the stream name.
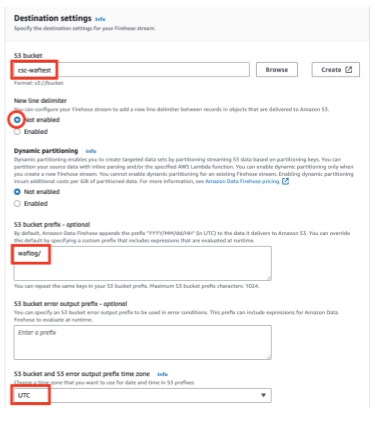
- S3 bucket: select any S3 bucket folder you wish to use (e.g.: csc-waftest)
- S3 bucket prefix (optional): enter a prefix (e.g.: waflog/)
If you want to add a prefix, make sure to add a slash (
/) at the end. - S3 bucket and S3 error output prefix time zone: UTC
Please choose UTC here because the feature may not work properly with different timezone.
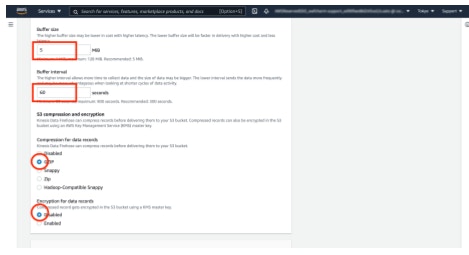
- Buffer size: 5MB is recommended
Buffer interval: 60 seconds is recommended
*WAF logs are exported to the S3 bucket when they reach the specified buffer interval or buffer size.
- Compression for data records: GZIP
- Create or select service access (IAM role).
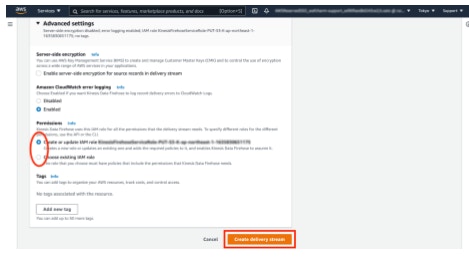
- Click [Create Firehose stream].
Output WAF logs on AWS WAF
- Open the list of web ACLs on AWS WAF.

- Open the target web ACL.
- Click [Logging and metrics].

- Click [Enable].

- Select [Amazon Data Firehose] under [Logging destination].
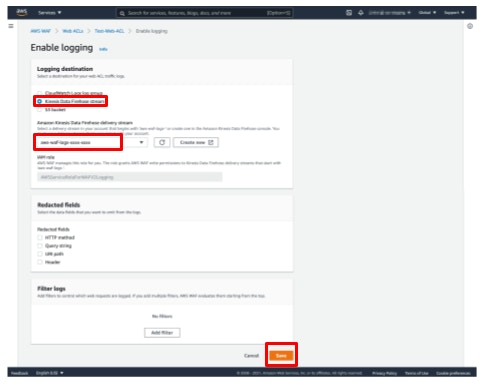
- Select the Data Firehose you just created.
- Click [Save].
- Access the target resources and make sure that WAF logs are outputted to the expected S3 bucket.
- Open the S3 bucket and check the path where WAF logs are outputted.
The format should be like below. You will use this information later.
csc-waftest/waflog/The S3 bucket name and prefix (or lack thereof) will depend on the options you chose in the previous steps.
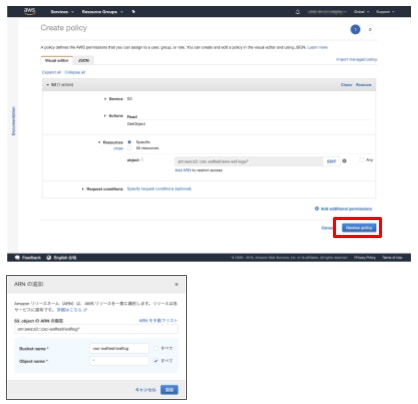
Create an IAM policy and role used by Lambda
You will be creating the three items below.
- Read permissions to your S3 bucket.
- Put permissions to transfer WAF logs to WafCharm's S3 bucket.
- The IAM role with the permissions above to be used by Lambda.
- Open IAM.
- Create a Read permission to your S3 bucket.
- Open [Policies] and click [Create policy].

- Configure the options below.
- Service: S3
- Action: GetObject
- Resources:
arn:aws:s3:::csc-waftest/waflog/*Write the S3 bucket path you obtained in the previous steps. The path specified under the [Resources] must end with
/*.
- Proceed to the Review policy page and enter the policy name and description (optional).
The name can be any value.
Example: wafcharm-waflog-s3-read
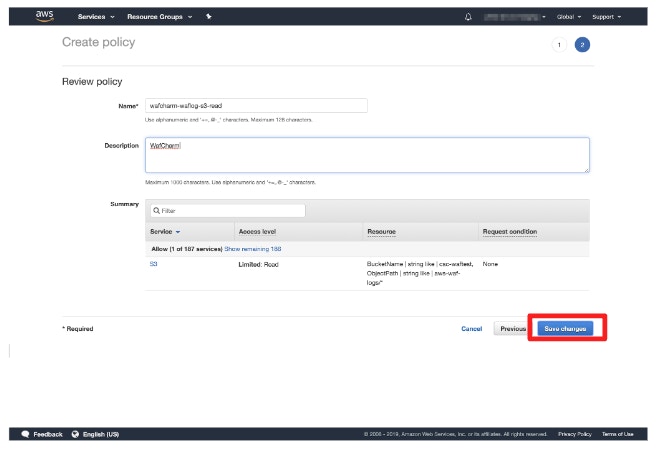
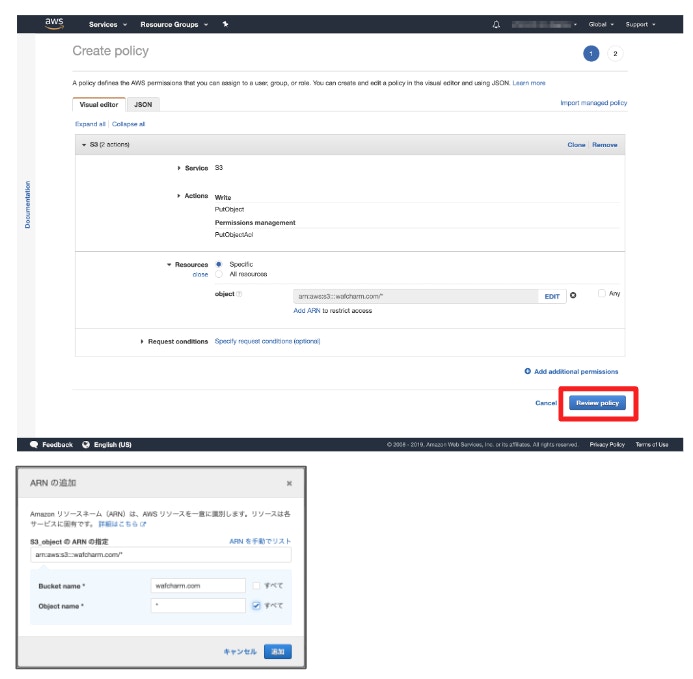
- Open [Policies] and click [Create policy].
- Create a Put permissions to transfer WAF logs to WafCharm's S3 bucket.
- Open [Policies] and click [Create policy].
- Configure the options below.
- Service: S3
- Action: PutObject, PutObjectACL
- Resources:
arn:aws:s3:::wafcharm.com/*Enter WafCharm's S3 bucket (as specified above) to enable WAF log transfer. The path specified under the [Resources] must end with
/*.
- Proceed to the Review policy page and enter the policy name and description (optional).
The name can be any value.
Example: wafcharm-waflog-s3-put
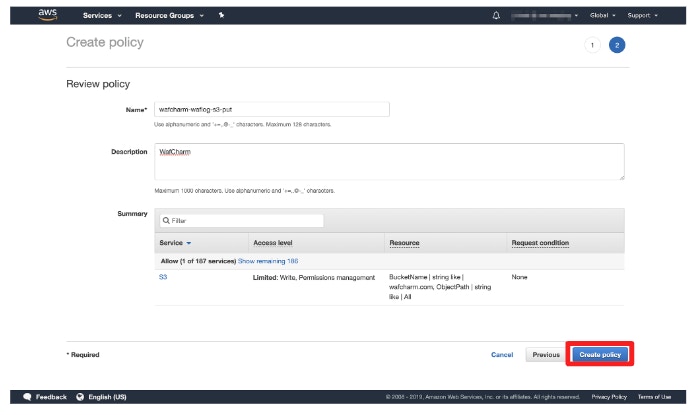
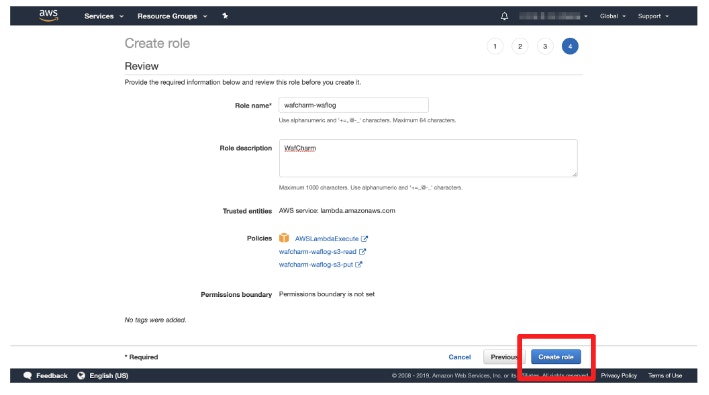
- Create an IAM role for Lambda.
- Open [Roles] and click [Create role].
- Choose [Lambda] for [Use case].
- Search for the permissions below under [Permissions policies] and check to add them.
- AWSLambdaExecute
- Read permission created in the previous steps (e.g.: wafcharm-waflog-s3-read)
- Put permission created in the previous steps (e.g.: wafcharm-waflog-s3-put)
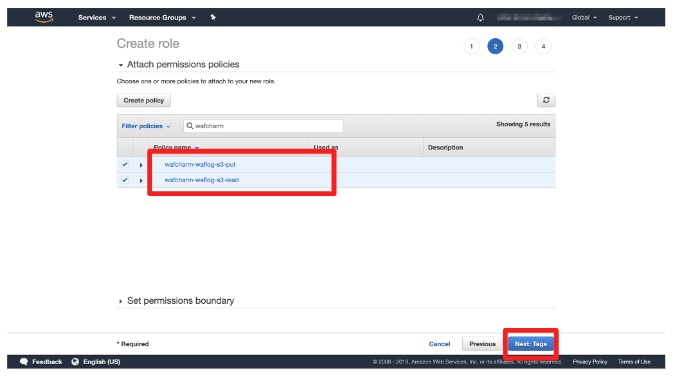
- Proceed to the next page and enter the role name and description (optional).
The name can be any value.
Example: wafcharm-waflog
Configure Lambda
- Switch to the same region as your S3 bucket.
- Open Lambda.
- Click [Create function].
- Enter [Function name].
The name can be any value.
Example: wafcharm-waflog
- Configure the options below.
Runtime: Node.js 20.x ~ Node.js 24.x
Execution Role: Use an existing role
Existing role: Select the IAM role you created in the previous steps (e.g.: wafcharm-waflog)
- Click [Create function].
- Paste the index.mjs available below in the editor under the [Code source].

- Click the [Deploy] button.
- Click the [Add trigger] button.
- Configure the options below.
Select a source: S3
Bucket: the S3 bucket you created in the previous steps
Event types: All object create events
Prefix: prefix of the S3 bucket you created in the previous steps (e.g.:
waflog/)
- Click [Add].
- Click [Configuration].
- Click the [Edit] button to the right of [General configuration].
- Configure the options below.
Description (optional)
Timeout: 1 minute

- Click [Save].

Configure the retention period for Lambda's execution logs on CloudWatch Logs
This configuration is optional.
If you want to change the retention period for your logs, please follow the steps below.
- Execute the Lambda script.
Access the target resources to output WAF logs. The Lambda script is triggered when the WAF logs are outputted to the S3 buckets.
- Open CloudWatch.
- Click [Log groups].
- Check the checkbox of the Lambda's log group.
- Click [Edit retention setting(s)] from the [Action] menu.
- Change the period under the [Expire events after:] drop-down menu.
The default is set to [Never expire]. Please adjust the period as necessary.